Sometimes you need to save the temporarily downloaded files (cache) for the Internet explorer to save some important files.Some may even need to use the space from another drive rather than use the C: drive itself.
To redirect Temporary Internet Files location to a different drive, follow these steps:
- Save and close all running applications
- Create a folder in the destination drive (for example, let's say 'E:\TIF')
- Click Start, Run and type 'CONTROL INETCPL.CPL' and press enter.
- In the Temporary Internet Files section, click on the 'Settings' button
- Click Move Folder button and browse to the target folder
- Click 'OK '
- Click 'Yes', when you see the window with the prompt ‘Windows will log you off to finish moving Temporary Internet Files. Do you want to continue?’

Windows will now copy all the Cookies,temporary Internet files to the destination folder and log you off. You need to log back into the Internet for the changes to take effect.
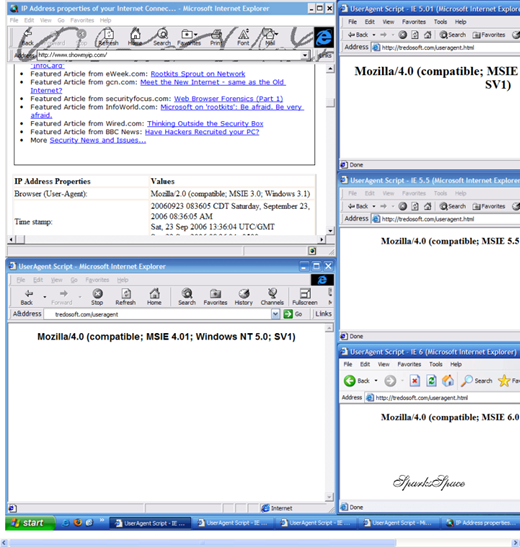
Ever wanted to test your website in various versions of Internet Explorer?While one browser displays the homepage correctly, the other messes it up completely. You feel like tearing out your hair especially when this happens while web designing.Thus, having
There are some solutions for this. The first: set up a virtual test environment, for instance, with the free program Virtual PC. In fact Microsoft provides a completely configured Virtual PC on which Internet Explorer 6 runs. The disadvantage is that the run time of the virtual machine is limited; apart from this, the program runs smoothly only on potent PCs.
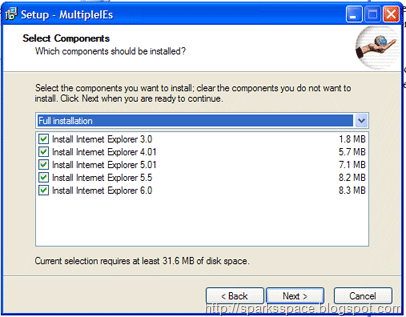
The freeware ‘Multiple IE’ is suitable for weaker systems. It facilitates several versions of Internet Explorer to co-exist together and installs them. First, update your PC i.e. with Internet Explorer 7 for XP and version 6 for Windows 2000. Download the ‘Multiple IE Installer’ from ‘http://tredosoft.com/Multiple_IE’ and install it.
After starting the program, in the ‘Select Components’ dialog, select ‘Custom Installation’ and decide which old IE versions you want to install. The older browsers can be called-up individually through the start menu after the setup.
However, don’t make any settings in the programs as far as possible, since a modified main page can also affect your main browser. On the other hand, the old versions also accept all settings and add-ons as long as they are compatible
with them.
Download Multiple IE installer |Freeware|10.3 MB
Also read Test Websites in various Internet Explorer Versions
Microsoft has finally released the first release candidate-IE8 RC1 Build 8.0.6001- for Internet Explorer 8 promising to make the Internet experience faster, secure, compatibility enhancements,Private tweaks and more compliant with web standards.
The new version brings enhancements in private browsing, accessibility, overall reliability and speed. RC1 reaches a significant development milestone towards a browser that can compete on closer footing with Firefox, Safari, Chrome and Opera in terms of features. However, web standards support (especially CSS 3) and performance are still far behind the competition.
Features
- Tabbed Browsing-option to re-open accidentally closed tabs.
- Security-introduction of the Clickjacking feature.
- InPrivate-Microsoft had debuted the InPrivate mode for anonymous browsing
- Phishing Filter-IE8 integrates its own Phishing filter called the SmartScreen.
- Import/Export settings-added to import favorites from Firefox and Safari
IE8 has also taken a page from Chrome's playbook and now opens a separate process for every tab. This means that IE8 won't crash outright just because of problems with one tab.
Internet Explorer 8 RC1 can only be installed on Windows Vista, Windows XP, and Windows Server.
One feature Internet Explorer still lacks is a download manager—a feature you'll find in every other browser.
Read:Windows Internet Explorer 8 Release Candidate 1 release notes
Are you frequently experiencing application crashes, blue screen errors or sudden reboot problems? A memory dump file will be generated by Windows for every crash.In reality, most crashes are caused by malfunctioning device drivers and kernel modules. In case of a kernel error, most computers running Windows do not show a blue screen unless they are configured to do so. Instead these systems suddenly reboot without any notice.
For those who don’t know how to use a debugger, download WhoCrashed Home Edition, a free Crash Dump Analyzer program from Resplendence Software.WhoCrashed shows the drivers which have been crashing your computer with a single click.
When your system crashed ,the following error reporting dialog popped up on next restart.
By using this utility you do not need any debugging skills to be able to find out what drivers are causing trouble to your computer. It relies on the Windows Debugging Package which will be automatically installed if it is not already installed on the computer system.
In most cases it can pinpoint the offending drivers which have been causing misery on your computer system in the past. It does post-mortem crash dump analysis and presents all gathered information in a comprehensible way.Who Crashed analyses Windows crash dumps and displays its findings in a notepad like window.
Previously, these problems used to be tackled only by experts with debugging skills, but now you can simply run WhoCrashed and you’ll know why your PC crashed and what should be done to prevent such PC crashes!
SysReq:Windows Vista/XP/2008/2003/2000|Freeware|702KB|Download
Note that WhoCrashed cannot be 100% sure about the driver which is responsible for crashing your computer. Because all kernel modules run in the same address space, a kernel module is able to corrupt another. Also, a driver may be able to cause problems to another driver which runs in the same device stack. So keep in mind this software is not guaranteed to identify the culprit in every case but most often it does.
Hard drives don't last forever. In fact, they fail more often than you might think. If your hard drive has ever crashed, you know the hassle it can cause.Here are 2 utilities to diagnose your hard drive.
HDDScan is a freeware utility for storage devices diagnostics .The program can scan storage device for Bad-blocks, show S.M.A.R.T. attributes.It basically provides the user with information about the hard disks that are installed on his computer, with ways to tests those hard disks and with options to change certain settings of those hard disks.
Supported storage devices:
- ATA/SATA HDD.
- SCSI HDD.
- USB HDD (see Appendix A).
- FireWire or IEEE 1394 HDD (see Appendix A).
- RAID volumes made of ATA/SATA/SCSI HDDs (surface tests only).
- USB Flash (surface tests only).
SysReq: Windows 2K/XP/2003/Vista|1.74 MB|Freeware| Download
HD Tune is another hard Disk utility which has the following functions:
- Benchmark: measures the raw performance
- Transfer Rate
- Access Time
- CPU Usage
- Burst Rate
- Hard Disk information which includes partition information, supported features, firmware version, serial number, disk capacity, buffer size, transfer mode
- Hard Disk Health
- S.M.A.R.T. Information (Self-Monitoring Analysis and Reporting Technology)
- Power On Time
- Error scan
- Temperature display
You can use it to measures the raw performance of your drive(s), including transfer rate, burst rate, access time and more. In addition, it provides detailed information about supported hard drive features, as well as current temperature, S.M.A.R.T. Information (if available) and an error scanner.
SysReq: Windows 2000/2003/Vista/XP | Freeware |583 kb | Download
Both the 32-bit and 64-bit flavors of Windows 7 Beta are available for download via this link, and you will have to burn the bits on a DVD in order to get started .
In order to build the bootable USB, users will need to turn to the Diskpart tool.Softpedia 
MaximumPC provides step-by-step guide to install Windows 7 Beta from a USB Key.Click Here To Read The Full Article @ Maximumpc.
JaBack is a Java based backup software that allows you to backup files and folders to compressed zip archives. This is a convenient program that quickly and easily make back-up your data. Everything in it is automated - with a few clicks select files and folders you want to make a backup copy to be synchronized with others or just archived.
It also lets you schedule automatic backups that will be conducted from time to time: hours, days, weeks or months.The format of the backups is ZIP, so you can easily retrieve the files.It does not support CD or DVD backup.
After backup, you can ftp or email the backup file. Synchronize, copy, and zip tasks are also included to satisfy all your backup and archiving needs. Another interesting feature of the program is the ability to back up when it detects a change in a given file or folder. It supports dynamic variables to achieve advanced automated tasks. Schedules can be synchronized to allow or prevent overlapping schedules.
SysReq:Win 9x/ME/2K/NT/XP/Vista |22.7 MB|Freeware|Download
Do you sometimes find you are making your PC multitask a little too much? Running lots of programs at the same time affects performance.JustCloseSomeTasks is an utility that helps you close inactive tasks easily.
This free program monitors all of your running programs. When you press the hotkey button (Ctrl-` by default - change via system tray -> preferences) and all windows are listed with the ones older than 120 seconds checked. press the close button to close these tasks. It saves taskbar space by offering you to close the stuff you've not used for a while.
You can also manually select or deselect tasks to close by opening the main program window.You can right click on any running process and choose to exclude it from the current session or all sessions.If you want to remove a program from the whitelist, just open up the settings.ini file in the installation folder and remove the process name from the whitelist section.This small application can be run from a USB.
SysReq:WinXP/Vista|Freeware|373KB | Download
How To Remove Any Malware Infection. A Step-By-Step How To. Part 1
How To Remove Any Malware Infection. A Step-By-Step How To. Part 2
How To Remove Any Malware Infection. A Step-By-Step How To. Part 3
How To Remove Any Malware Infection. A Step-By-Step How To. Part 4
How To Remove Any Malware Infection. A Step-By-Step How To. Part 5
Security researchers are reporting that the Conficker worm virus, which preys on a recently reported vulnerability (MS08-067) in the Microsoft Windows server service, is spreading rapidly."Of the two million computers analyzed, around 115,000 were infected with this malware, a phenomenon we haven't seen since the times of the great epidemics of Kournikova or Blaster," Luis Corrons, Technical Director of PandaLabs, said in a report summary.
When executed on a computer, Conficker disables a number of system services such as Windows Automatic Update, Windows Security Center, Windows Defender and Windows Error Reporting. It then connects to a server, where it receives further orders to propagate, gather personal information, and downloads and installs additional malware onto the victim's computer. The worm also attaches itself to certain Windows processes such as svchost.exe, explorer.exe and services.exe.
Once this virus infects a computer it does a number of things
- Extracts all of its files to the %System% directory with random DLL file names, which can wreak havoc on your computer.
- Deletes the user's Restore Points.
- Registers a services called Netsvcs
- Creates scheduled tasks that execute all of the DLL files.
- Creates it's own simple HTTP server on the infected computer and spreads the worm to other computers in the network through file shares.
- Creates an Autorun.inf file in file shares to execute the warm files once the share is accessed by another computer.
- Connects to external sites to download additional files.
The registry entries added by Mal/Confiker-A are under:
HKLM\SYSTEM\CurrentControlSet\Services\<random service name>
The random service name will also be added to the list of services referenced by:
HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\SvcHost\netsvcs
Mal/Conficker-A modifies permissions on the service registry entries so that they are not visible to the user.When spreading to removable media Mal/Conficker-A attempts to create the following hidden files:
<Removable Drive Root>\autorun.inf
<Removable Drive Root>\RECYCLER\S-x-x-x-xxx-xxx-xxx-x\<Random Letters>.dll
Win32/Conficker.A tries to obtain the IP address of the affected system by accessing the following websites:
www.getmyip.org
getmyip.co.uk
checkip.dyndns.org
Mal/Conficker-A will attempt to copy itself to the following location:
<System>\<random filename>
(e.g. C:\windows\system32\zdtnx.g)
Precautions & Removal
- Ensure Windows is fully updated to fix the MS08-067 vulnerability that the Conficker family of worms uses to spread.
- Ensure that all removable storage devices are scanned after being connected to a computer infected with the Conficker family of worms.
- Ensure HIPS and buffer overflow prevention are both turned on and that "alert only" mode is turned off.
- Ensure the on-access scanner is turned on and that "on write" scanning is enabled.
If W32/Confick-E is detected on the computer, clean up this item first and then immediately run another full scan. Cleaning up W32/Confick-E removes the worm from memory and allows Sophos Anti-Virus to scan files that may have been locked by the virus while it was running.
If a full scan reports unscannable files and W32/Confick-E is not found in memory, ensure the on-access scanner is enabled and the virus data is up to date, reboot the computer and immediately perform another full scan. This causes the on-access scanner to prevent the Conficker worm from loading as a service and should unlock those files so they can be scanned. After cleaning up an active infection of the Conficker worm, a reboot may be required.
To remove the worm and its malicious components completely, it is recommended to use Norman Conficker Cleaner. Removal tools are also available from Microsoft and Symantec.
Since the virus can spread via USB drives that trigger AutoRun, disabling the AutoRun feature for external media through modifying the Windows Registry is recommended.
If you have an administrator account with an easily guessed password, change it. Microsoft provides a guide to strong passwords that includes a link to the company's online password checker. If somebody other than you controls your computer's admin password, make sure that person understands the gravity of this situation.
Test the Strength of Your Password :here
Online browsing without protection against the latest fast-spreading virus and worms, such as Netsky, Mytob and MyDoom, can result in infections within minutes.Once infected, the virus will usually attempt to spread itself to your friends, family and associates by accessing your e-mail contacts and networked PCs. The infection may also allow hackers to access files on your PC, use it to launch attacks against other computers and Websites or to send mass spam email
PC Tools AntiVirus Free Edition is an anti-virus scanner, that provides real-time protection against viruses, worms and Trojans. It also offers on-demand scans, as well as automatic updates and real-time scanning of incoming and outgoing mail. Other features include heuristic scanning and scheduled scans.The Free Edition offers limited support and non-priority updates
SydReq:![]() 2000/XP/2003/Vista|Freeware|22.20MB|Release Date:Jan 08, 2009
2000/XP/2003/Vista|Freeware|22.20MB|Release Date:Jan 08, 2009
Are you worried that some malicious cracker or your employer could be violating your privacy and reading private emails?The Whisper Bot is a free, simple, and secure service to provide a modern day passing of the notes between you and your friends and keep away prying eyes.
You can save messages to be send in later time, and it has cool font colors and more, and is really easy to send the whisper to the paltalk room.
- You go to WhisperBot.com and Send a note
- The note, along with everything else, is encrypted with a high level of encryption and stored in the database
- An e-mail gets sent off to alert the recipient of your note
- The recipient clicks on the URL and retrieves their note
- And the recipient and world are in their happy place
Ad-Aware Anniversary Edition provides comprehensive malware protection without loading down your system’s resources, bringing you the core competence you need to stay safe online.Numerous changes in Ad-Aware Anniversary Edition include: Behavior-based heuristical detection; Ad-Watch Live! integrated real-time protection; Customizable Profile Scans and full integration with Windows Security Center.It provides advanced threat protection, and is significantly lighter and faster than our previous versions.
New and Improved Features:
- Malware Detect, Remove AND Clean
- Behavior-based Heuristical Detection
- Integrated Ad-Watch Live! Real-time Protection.
- Rootkit Removal
- Lavasoft AutoStart Manager
- Radically improved resource efficiency
- Lavasoft SmartSet
- Background Scan Mode
- Customizable Profile Scans
- External Drive Scanning
- Pin-Point Scanning
- Full integration with Windows Security Center
- Easy to Download, Install and Use
Ad-Aware is one of the must have program for protecting system against malware attacks. Ad-Aware will protect your system from spyware, keyloggers, trojans and other identity theft software. Ad-Aware has both free and paid versions, and the free version is enough for average user.
Windows Vista allows you to use multiple operating systems.If Vista is installed as a dual boot with Windows XP, by default Vista would be set as the primary operating system.
However , if you frequently use Windows XP , you can set Windows XP as the default operating system by a simple command:
Click>Start and type”cmd” in the search box
Once a command prompt is displayed, simply type in the command
“bcdedit /default(ntldr)” and press Enter
Windows XP will now be set as your default operating system.
Every internet user’s personal information is increasingly at risk and they must take precautions to prevent identity theft. Hackers and identity thieves go after "low hanging fruit" and know that many people do not have the time and experience to protect sensitive data appropriately.
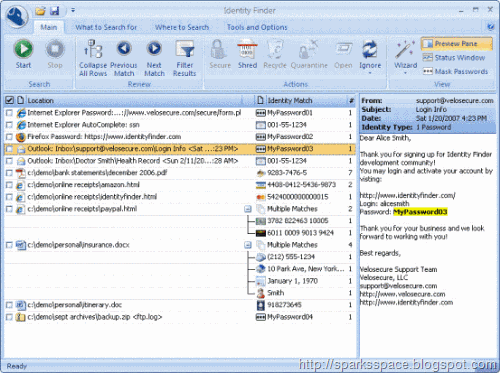
Identity theft can have a significant financial impact and now more than ever, people must take additional steps to protect themselves.Identity Finder Free Edition will detect personal information on your computer that is vulnerable to identity theft or fraud.It has the robust and comprehensive search and secure capabilities.
Identity Finder Free can be downloaded for personal use at no charge. The Free Edition will discover unprotected instances of consumers' credit card numbers and passwords that they didn't know existed in hidden areas and files on their computers. The Free Edition also comes with fully functioning security tools to clean personal information stored inside their web browsers, permanently shred any file on their computer so it can never be recovered by a hacker, encrypt any file so it cannot be read without a password, and manage multiple passwords inside Identity Finder's secure password vault.
SysReq:Windows 2000 with SP3/XP/Vista | Freeware | 30.1MB
Disk Investigator helps you to discover all that is hidden on your computer hard disk. It can also help you to recover lost data
- Display the true drive contents by bypassing the operating system and directly reading the raw drive sectors.
- View and search raw directories, files, clusters, and system sectors.
- Verify the effectiveness of file and disk wiping programs.
- Undelete previously deleted files.
Sys Req: Windows All | Freeware | 347 KB
Noto Personal Organizer is a mini application that you can move around your computer desktop. It is very easy to use because it works exactly like a real personal organizer, with page turning and separate side tabbed sections, such as: day to view, week to view, month to view, projects section, info section and address book
It is very easy to use because it works exactly like a real personal organizer, with page turning and separate side tabbed sections, such as: day to view, week to view, month to view, projects section, info section and address book. It also has added benefits such as a selection bars and icons that can be dragged and dropped within Noto to highlight certain events. Alarms can be set so you dont miss important appointments.
There are also embedded gadgets, including a calculator, mp3 player and a memory game. Noto is customizable with a pre loaded selection of cover designs, icons, gadget designs, and maps. You can add more to your selection by connecting online from within Noto to drag and drop more content from our download section.
SysReq:WinXP, Windows2000,2003, Vista |Trail Ver | 16.97MB
In normal circumstances, a badly scratched disc might show up as completely unreadable by your computer.CD Recovery Toolbox Free is a data recovery tool, designed to recover files from scratched or otherwise damaged or corrupt CD, DVD, HD DVD and Blu-Ray disks.You can use it to restore information lost as a result of some mechanical damage of the disk (scratches, chips, different spots on the surface) or as a result of incorrect recording.
Not all of the files and folders can be found - that depends on the degree and location of the damage. Therefore, the CD Recovery Toolbox Free tool finds the possible maximum amount of information. After that, it shows a list of all files and folders available for recovery. Now the user can select the files and folders to be recovered. Those specific objects will be recovered while the others will be ignored. The program recovers the maximum amount of information in the damaged file. This reduces the risk of data loss considerably
Features:
- Recovering files larger than 4 Gb
- Detecting possible lack of free space on the hard disk for storing the recovered files
- Recovering corrupted data from all most common types of media for today
- Working with data that became corrupted both after a physical damage of the media and due to program errors
- Allowing the user to completely control the recovery process
- Giving the user as detailed report about the data recovery process as possible
SysReq:Windows 98, Me, NT 4.0, 2000, XP, 2003, Vista|Freeware|662KB
Another similar software which is capable of recovering data from damaged or scratched discs is Roadkil's Unstoppable Copier. It allows you to copy files from disks with problems such as bad sectors, scratches or that just give errors when reading data. The program will attempt to recover every readable piece of a file and put the pieces together. Using this method most types of files can be made useable even if some parts were not recoverable in the end.
SysReq:Windows Xp, Vista, NT, 9x ,Me, 2000|Freeware|78.9KB
Other CD/DVD data recovery software
BadCopy Pro | CDCheck | IsoBuster | Stellar Phoenix CDRom Data Recovery
You may have heard about the overwhelming onslaught of 'bots' or 'zombies' Those are a computer or network security threats.A 'bot' is a type of malware which allows an attacker to gain complete control over the affected computer.Computers that are infected with a 'bot' are generally referred to as 'zombies'.Attackers are able to access lists of 'zombie' PC's and activate them to help execute denial-of-service (DoS ) attacks against Web sites, host phishing attack Web sites or send out thousands of spam email messages.
RUBotted monitors your computer for suspicious activities and regularly checks with an online service to identify behavior associated with Bots.It intelligently monitors your computer's system behavior for activities that are potentially harmful to both your computer and other people's computers.Upon discovering a potential infection, RUBotted prompts you to scan and clean your computer.
RUBotted co-exists with your existing AV software, providing advanced bot specific behavior monitoring. RUBotted does not rely on frequent, network intensive updates to ensure your computer's continued protection.
RUBotted | 4.94 MB| Freeware
Antivirus 2009 is a rogue anti-spyware application.It is is an updated version of Antivirus 2008. Antivirus 2009 is usually promoted via a ZLOB/MediaAccess Codec installer found on adult websites.It floods the user with popups and fake system notifications.The user might click on one of the popups or notifications, all of which claim they will take him to a legitimate security tool, but try to make him purchase Antivirus2009's "licensed version" instead. It redirect web browser to antivirus-premium-scan.com, antivirus-best.com webscannertools.com, livesecurityinfo.com,antivirusonlivescan.com,bestantivirusscan.com
secureclick1.com or premiumlivescan.com and websites that sell the malware.
Symptoms
Manual Removal
Search the following files and delete
Antivirus2009.exe
av2009.exe
av2009[1].exe
AV2009Install.exe
Antivirus 2009.lnk
Uninstall Antivirus.lnk
- Go to Start > Search > All Files or Folders.
- In the "All or part of the the file name" section, type in "Antivirus 2009" file name(s).
- For better results, select "Look in: Local Hard Drives" or "Look in: My Computer" and then click "Search" button
Stop Antivirus 2009 Processes
Unregister and delete .dll files
shlwapi.dll
wininet.dll
Delete registry values:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\ CurrentVersion\Run\15358943642955870504508370025739
HKEY_LOCAL_MACHINE\SOFTWARE\Antivirus
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\”Antivirus” = “%ProgramFiles%\Antivirus 2009\Antvrs.exe”
HKEY_CURRENT_USER\Software\Antivirus
Other programs to remove Antivirus 2009:
- Malwarebytes Anti Malware – Download | Malwarebytes' Anti-Malware 1.30
- Windows Defender – Download
- Spyhunter –Download | SpyHunter_Security_Suite_v3
Prevention
- Keep your Windows Security up-to-date
- Download and install a reliable anti-spyware software
Related Posts
Incidents of malware infections, spyware incidents and user mistakes is growing at an alarming rate,even the most cautious of users will encounter undesired behavior from a Windows XP PC.This leads to unexplained "blue screens" , frequent system slowdowns , nonworking applications errors and much more .
Reimage.com's instant, online, PC repair tool is a revolutionary new concept in PC repair.It cleans the unidentifiable registry entries or known problems. It also scans the hard drive and removes viruses, malware, adware or anything that can cause a problem. If the system is unbootable, Reimage.com provides tools on its Web site to create an emergency boot CD, which will enable the subject PC to boot and connect to the Reimage service.
Total repair - Solves all your XP problems
Place the fresh, healthy items on your PC
Risk free, money back guarantee
Repairs Windows XP computers instantly
Reimage is available for Windows XP.With Reimage, any software component can be brought back to its original working state. The simple and swift restoration of missing parts and the removal of redundant parts, is far more efficient than the conventional method of reinstalling.
Build your free bootable XP CD - and fix dead PCs
1. Create a bootable CD image file (.ISO)
2. Burn the .ISO image file on a blank CD
- Locate the ISO image file that you have just created (bootcd.iso)
- "ISO Recorder" is a free tool (power toy) that allows to burn CD images. Download it from here.
- Read here how to use it.
3. Done! You have a bootable XP CD.
Now you can revive a dead PC!
- Use the bootable XP CD to boot from the dead XP and simply access your account at www.reimage.com, start a repair. Now you can revive the dead PC!
Sys Req:500MB of free disk space|A licensed copy of Microsoft Windows XP CD|127MB