Backdoor Trojans
A backdoor trojan differs from a trojan in that it also opens a backdoor to your system.A trojan is a malicious application that appears to do one thing, but actually does another.Examples of backdoor trojans are Netbus or Back Orifice.They are so dangerous because they have the potential to allow remote adminstration of your system.This gives an attacker unauthorized access to a machine and the means for remotely controlling the machine without the user's knowledge. A Backdoor compromises system integrity by making changes to the system that allow it to be used by the attacker for malicious purposes unknown to the user.
- Use your system and Internet connection to send spam (yes, the majority of spam is now generated by infected systems).
- Steal your online and offline passwords, credit card numbers, address, phone number, and other information stored on your computer that could be used for identity theft, or other financial fraud.
- Log your activity, read email, view and download contents of documents, pictures, videos and other private data.
- Use your computer and Internet connection, in conjunction with others to launch Distributed Denial of Service (DDoS) attacks.
- Modify system files, disable antivirus, delete files, change system settings, to cover tracks, or just to wreak havoc.
How to tackle this ?
Download SDFix.exe and save it to your desktop:
SDFix
- Double click on SDFix on your desktop,and install the fix to C:\
Please then reboot your computer into Safe Mode by doing the following:
- Restart your computer
- After hearing your computer beep once during startup, but before the Windows icon appears, tap the F8 key continually;
- Instead of Windows loading as normal, a menu with options should appear;
- Select the first option, to run Windows in Safe Mode, then press "Enter".
- Choose your usual account.
- In Safe Mode,go to and open the C:\SDFix folder,then double click on RunThis.bat to start the script.
- Type Y to begin the script.
- It will remove the Trojan Services then make some repairs to the registry and prompt you to press any key to Reboot.
- Press any Key and it will restart the PC.
- Your system will take longer that normal to restart as the fixtool will be running and removing files.
- When the desktop loads the Fixtool will complete the removal and display Finished, then press any key to end the script and load your desktop icons.
Download the UNDO.ZIP file and unzip it with a program like WinZip. Double click the undo.reg file to import it into the registry. For the curious, the contents of the REG file are:
Click Start, then Run, then type "c:\windows\win.ini" in the text box,then click OK. Scroll down to the line that begins with "run=" and if it loads the trojan program, delete it.Click Start, then Run, then type "c:\windows\system.ini" in the text box,then click OK.Scroll down to the line that begins with "shell=" and if it loads the trojan program,be very careful to delete only the part that loads the trojan.After you are done the shell= should look like this:shell=Explorer.exe
Another Utilities & Procedures
Procedure #1
Download the following four items
McAfee Stinger
Trend Sysclean Package
Latest Trend Virus Pattern Files. (example; lpt285.zip*)
(*The file name lpt285.zip is simply an example name of the file and you'll find the filename posted at TrendMicro will have a higher number than 285. Each time TrendMicro produces new Pattern Files the number in the file name will be incremented accordingly.)
Ad-Aware SE (free personal edition)
- Create a new directory.
On drive "C:\"
(e.g., "c:\New Folder")
or the desktop
(e.g., "C:\Documents and Settings\username\Desktop\New Folder") - Place SYSCLEAN.COM (the Trend Sysclean Package referenced above) into the new directory you created. Extract the latest Trend Virus Pattern Files (Example: lpt$vpn.285 and WHATSNEW.TXT) from the zip file you downloaded above into the same new directory you created. The Trend Pattern File contained in the ZIP file must be placed in the same directory as SYSCLEAN.COM!
- Important: The TrendMicro Pattern file is updated reguarly. Aywhere from once per day to a few times in a day. Always make sure you have the latest version of SYSCLEAN.COM and the Pattern File before you scan your platform. The McAfee Stinger Internet worm and Trojan removal tool is upgraded periodically. Always make sure you have the latest version of McAfee Stinger utility before you scan your platform.
- Install and Update Ad-Aware with the latest definitions.
- If you are using WinME or WinXP, disable System Restore.
Disable SysRestore Procedure - Reboot your PC into Safe Mode [F8 key during boot process].
How to Boot Into Safe Mode:
Generic
Windows XP
How to perform a clean boot in Windows XP - Using McAfee Stinger, the Trend Sysclean utility and Ad-Aware, perform a Full Scan of your platform and clean and/or delete any infectors and/or parasites found (a few cycles may be needed).
- Restart your PC and perform a "final" Full Scan of your platform using McAfee Stinger, the Trend Sysclean utility and Ad-Aware.
- If you are using WinME or WinXP,Re-enable System Restore and re-apply any System Restore preferences (e.g. HD space to use suggested 400 ~ 600MB).
- Reboot your PC.
- If you are using WinME or WinXP, create a new Restore point
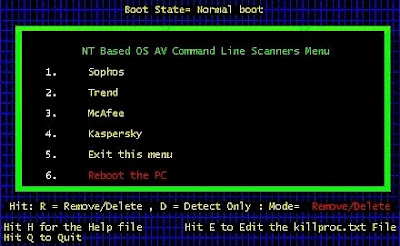
Download MULTI_AV.EXE from the here
Multi AV
To use this utility, perform the following...
Execute; Multi_AV.exe { Note: You must use the default folder C:\AV-CLS }
Choose; Unzip
Choose; Close
Execute; C:\AV-CLS\StartMenu.BAT
{ or Double-click on 'Start Menu' in C:\AV-CLS }
NOTE: You may have to disable your software FireWall or allow WGET.EXE to go through your
FireWall to allow it to download the needed AV vendor related files.
C:\AV-CLS\StartMenu.BAT -- { or Double-click on 'Start Menu' in C:\AV-CLS}
This will bring up the initial menu of choices and should be executed in Normal Mode.
This way all the components can be downloaded from each AV vendor's web site.
The choices are; Sophos, Trend, McAfee, Kaspersky, Exit this menu and Reboot the PC.
You can choose to go to each menu item and just download the needed files or you can
download the files and perform a scan in Normal Mode. Once you have downloaded the files
needed for each scanner you want to use, you should reboot the PC into Safe Mode [F8 key
during boot] and re-run the menu again and choose which scanner you want to run in Safe
Mode. It is suggested to run the scanners in both Safe Mode and Normal Mode.
When the menu is displayed hitting 'H' or 'h' will bring up a more comprehensive PDF help
file.
Additional Instructions: here
Also check the following
Symantec
Backdoor SDBot.H Trojan
BackDoor-ABH
Backdoor:Win32/zonebac_gen!B FindAWF





A good practice is to look routinely at any modification of programs to discover new, odd services or processes.You can use network, application diagnosis and troubleshooting programs such as TCPview ,Inzider , Active Ports etc
ReplyDeleteTCP View:
http://www.snapfiles.com/get/tcpview.html
Inzider
http://www.ntsecurity.nu/toolbox/inzider/
Active Ports
http://www.devicelock.com/freeware.html
Also ListDlls and Process Explorer can certainly be useful if finding any suspect signs of trojan infected or backdoored processes.
ListDLLs v2.25
http://technet.microsoft.com/en-us/sysinternals/bb896656.aspx
Process Explorer v11.12
http://technet.microsoft.com/en-us/sysinternals/bb896653.aspx
Other Tools
1] Netcat - http://www.hackerscor.com/km/files/hfiles/ncnt090.zip
[2] iCMD - http://go8.163.com/lmqkkk/mytools/iCmd.exe
[3] RemoteNC - http://go8.163.com/lmqkkk/mytools/remotenc.zip
[4] Tini - http://go8.163.com/lmqkkk/mytools/tini.exe
[5] WinShell - http://go8.163.com/lmqkkk/mytools/Winshell4.0.zip
[6] CGI-backdoor - http://go8.163.com/lmqkkk/mytools/cgi.zip
[7] Remote Administrator - www.radmin.com
[8] TightVNC - http://www.tightvnc.com/download.html
[9] Rootkit v.0.44 – www.ndsafe.com/fires/rk_044.zip
[10] IIP Driver - http://www.pedestalsoftware.com/intact/iipdriver.htm
[11] Fport - http://www.foundstone.com/knowledge/proddesc/fport.html
[12] Active Ports - http://www.ntutility.com/freeware.html
[13] Vision - http://www.foundstone.com/knowledge/proddesc/vision.html
[14] LANguard Network Security Scanner
http://www.gfisoftware.com/stats/adentry.asp?adv=142&loc=17
[15]http://3d2f.com/tags/tcp/udp/ports/scanner/
No more trojans and keyloggers
ReplyDeleteThanks to www.search-and-destroy.com because of which I could find several keyloggers and trojans on my computer. I had also tried for some other antispyware but no one could detect my problem. Your software is excellent.