Autorun.inf virus removal
Autorun.INF is usually used by CD Installers to autoplay their installations but Hard disks by default should not have AUTORUN.INF in the drive.
Now, it is possible that your computer is infected by those viruses if you try to display the content of the your computer through command prompt, using the dir /ah command.
The said virus hides itself inside a folder named Recycled. The folder has a hidden/system/read-only attribute, that’s why you can’t see it if you will use the Search window. When your system is infected by the said virus, it infects every drive connected to your PC by dropping VCAB.DLL to the internet temporary folder and creating the CTFMON.EXE to folder Recyled & AUTORUN.INF to the root directory of every drive. That’s why when you connect your USB sticks to the infected PC it will be infected immediately, the USB disks will be the new carrier for the virus. The program runs every time you start your computer because it copy itself in the Startup folder of the Start Menu. It also run every time your insert the infected USB disk and it triggers every time you Double-Click the infected drive (bcoz of the AUTORUN.INF). The virus infects .EXEs and .DLLs.
To check if your system is infected by the said virus without using an antivirus, do the following steps:Go to command prompt.
- Type CD\ in drive C to go the root directory
- Type DIR /AH and press ENTER key. This will display all hidden files in your drive C
- If you see a file AUTORUN.INF and a folder Recycled, then your system is infected.
- Try doing this to your USB drive and check if your USB stick contains the same folder and AUTORUN.INF, if it does then your system is really infected..
To remove it download and install a trial version of Trendmicro and scan your system.
To manually remove it follow the following steps.
Boot your system in Safemode
Go to command prompt, in Drive C do the following commands.
- Type -> ATTRIB -H -R -S AUTORUN.INF then press enter
- Type -> DEL AUTORUN.INF then press enter
- Type -> ATTRIB -H -R -S Recycled then press enter
- In Windows Explorer in Safemode, remove the folder Recycled in drive C use Shift-Delete to delete the folder.
- Repeat Step 3 to 6 for all drives of your system including the USB drive.
- Search for CTFMON.EXE in your system using the Search of Windows found in Start Menu. If you find a file that is not located in C:\WINDOWS\SYSTEM32, delete it immediately. Dont forget to empty the recycle bin afterwards (Usually the virus will copy itself in the Startup folder of the Startmenu. Check if the file is present there and delete it then.)
Click Start->Run->type REGEDIT.EXE
- Go to this key from the register HKEY_CURRENT_USER\Software\ Microsoft\Windows\CurrentVersion\Policies\Explorer
- Look for the entry NoDriveTypeAutoRun, double click the entry
- Type a new value : 0FF (Hex) for the NoDriveTypeAutoRun, this will turn off the AutoRun for all drives, and press ENTER
- Reboot the system.
Viruses that uses Autorun.INF
There are several viruses that uses the autorun.inf to spread itself such as the Bacalid (hides itself in ctfmon.exe) and the RavMon.EXE. These viruses set its file attributes to System+Hidden+Read-Only attributes so some anti-viruses will have a hard time detecting or finding them. These viruses save itself in the root directory of every available drives of the current infected computer and runs itself every time you Double-Click the drive. In USB Sticks and CDs that are infected by the virus runs automatically especially if drive autorun is enabled for the current drives (which is usually by default, autorun for drives are enabled).
Disable AUTORUN from Registry
Now you can disable the AUTORUN for all drives by configuring the registry. Open the registry by typing regedit.exe to the command prompt (if your still at the command prompt) or execute it in Run. Look for the HKEY_CURRENT_USER\Software\ Microsoft\Windows\CurrentVersion\Policies\Explorer as shown below:
Click the NoDriveAutorun DWORD entry and type the value HEX: FF (255 in Decimal). (If the NoDriveAutorun does not exists, you can creat it by right-clicking the right side area of the regedit window, then click New->DWord Value -> type NoDriveAutorun) Close the registry and restart the computer. This procedure will disable all the autorun for all drives of your computer and at least will prevent the autorun function of infected USB drives or CDs and avoid the infection of viruses like the Bacalid and RavMon.exe
If you want to prevent viruses that uses autorun.inf to infect your USB flash drive, try to do this:
1. Open your flash drive via Command Prompt (do this via Start->Run->cmd.exe)
2. Change your logged drive to your USB flash drive (e.g. if your drive is at drive E: then type E: on the command prompt then press enter)
3. Create a folder named: AUTORUN.INF on the root directory of your flash drive. (to do this type the command: MD\AUTORUN.INF). If an error: a subdirectory already exists… shows, try to follow the instruction above to remove existing autorun.inf before doing this instruction.
The reason why this will avoid future infection is that autorun.inf viruses usually generates a file autorun.inf. Having an AUTORUN.INF folder on the root directory of your drives will make virus programs unable to create their own autorun.inf file, virus can’t even overwrite it because it’s a folder and not a file…
Download remove autorun virus.exe :4 Shared
How to Remove Win32 AutoRun Worm - Funny UST Scandal - XMSS.exe
XMSS.exe Win32 AutoRun Files
- x:autorun.inf
- x:xmss.exe
- x:Funny UST Scandal.avi.exe
- %Windir%\autorun.inf
- %Windir%\xmss.exe
- %Windir%\Funny UST Scandal.avi.exe
Fixes Win32 AutoRun.* Worm
Here’s a few step to prevent Win32 AutoRun Worm.
- Disabled System Restore for Temporary - KB 264887
- Boot Windows in Safe Mode - KB 315222
- In Windows Safe Mode, Open Windows Registry Editor
- Windows Start > Run > Regedit
- Browse to the following registry settings ↓
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
- Replace explorer.exe, xmss.exe with exporer.exe
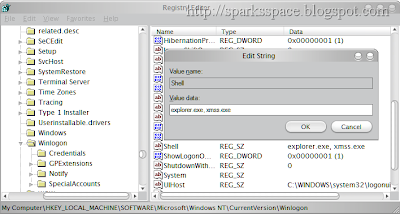
Delete all the following files
- C\autorun.inf
- C\xmss.exe
- C\Funny UST Scandal.avi.exe
- X:\autorun.inf
- X:\xmss.exe
- X:\Funny UST Scandal.avi.exe
- %Windir%\autorun.inf
- Windir%\xmss.exe
- %Windir%\Funny UST Scandal.avi.exe
- Clean All Windows Temporary Files
- Restart Windows
%Windir% refers to the Windows folder (e.g. C:\Windows, C:\WindowsNT) and X: is drive letters used by a removable or network drive

















After a week of banging my ignorant head against the wall, trying everything I could think of, I bumped into this post as a result of a Google search. I (slowly) followed the steps, first on my computer then on my friend's computer (I infected her computer with my USB drive). It worked like a champ on both, and all I can type is THANK YOU VERY VERY MUCH, and if I can do it then anyone can.
ReplyDeleteTHANK YOU VERY MUCH!
ReplyDeletegreat information, helps a lot............ THANK YOU VERY VERY MUCH
ReplyDelete